Subscribe for Weekly Updates

Cybersecurity Begins Inside Your Company
 By Al Wilson, CISSP, CISM
By Al Wilson, CISSP, CISM
The Verizon Breach Report offers several important lessons, one of which is that education regarding cyberattacks and the application of basic computer hygiene principles could have prevented about 88 percent of the more than 1,900 breaches that were analyzed within the report. Information security professionals understand this, and stress a balanced program of three guiding principles: availability, integrity, and confidentiality.
A major piece of any cyber defense is understanding that success is dependent on the interest and participation of the end users. Relying on someone else (IT departments, consultants, etc.) and assuming that computer security will be taken care of for you can lead to a tragic outcome. Reading several PICPA blog posts, it’s clear that many members have received excellent insight regarding what they can do to boost their own, and therefore the client’s security. (See “Modern Data Security Threats,” “Cloud Computing: Security and Risk Management,” and “Securing Data in the Cloud.”)
Of the three principles mentioned above, I will start with availability. In the end, the ability of a business to provide value to its clients is rooted in the ability to conduct business without interruption. While this is a topic that includes high availability (the ability to failover from system to system without interruption) and the ability to defend against denial-of-service attacks, at the most basic level is the concept of backup and recovery. Too often individuals believe that backups are being taken care of for them, or they assume someone in-house knows how to retrieve data. You must periodically test whether you can retrieve any or all of your data to a separate location. Doing so is the mark of a mature process.
Maintaining accuracy and completeness of information over its entire life is the basis of data integrity. In the area of advising on personal finances, you must make sure the data you receive is not altered in transit or in its storage location. Subsequent use of the information’s dissemination must also shield against alterations. It would behoove those in the industry to know and understand if this is being done and how it is being done on your behalf. Recent news reports indicate that some of the evidence against Paul Manafort, former Trump campaign manager, was obtained because he was unable to convert financial documents to PDFs. By sending documents back and forth via email, Manafort and his associates made it easy for prosecutors to determine that the documents had been altered, who they were altered by, and when.
The confidentiality of your information-protection program is arguably the one most visible and understandable area of defense among those in your company who aren’t dedicated to the information security field. Ask yourself the following questions:
- When I use email, should I just use a username and password, or should I adopt multifactor authentication?
The multifactor concept provides an extra layer of security if you get tricked into revealing your password via phishing or it gets guessed because it follows a simple pattern. The extra step could be a text back to your phone with a unique code, an app that provides a unique time-based code, or an app that merely asks you to “OK” a login. For example, the hack of the Democratic National Committee began as a phishing attack, which likely could have been mitigated if the two-step authentication of Google was turned on. - Do you or your team feel comfortable recognizing unusual requests?
Phishing and other social engineering tactics prey on people’s desire to help and their inattention to details. A common mode of operation includes compromising one of your vendors, then sending in requests for action under their guise. Make sure everyone in your corporate structure knows it is OK to pick up the phone and verify who the person is that the request is coming from and what their relationship is to what you do. - Do you know whether your computer systems are being patched for vulnerabilities? Is there a requested date/time for you to leave your computer on to receive patches, is there a scheduled downtime for the servers and websites that you depend on?
A common observation from IT personnel is that they don’t feel empowered by the company to do the necessary maintenance due to a corporate misperception that the system would be unavailable. Reports indicate that the Equifax breach was partially exasperated by not patching systems in a timely fashion. Perhaps understanding how things are done and giving support to those who might need it will save a lot of grief in the end.
 |
|
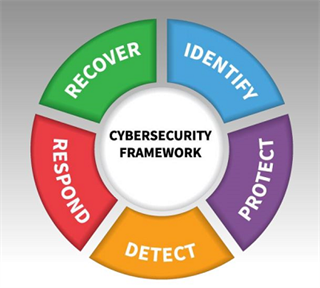
Image from the National Institute of Standards and Technology |
Want to learn more so that you can be a good partner to your clients and can ask the proper questions to your IT support staff? Or are you an independent adviser who would like to feel more confident regarding the program of protection you have? The National Institute of Standards and Technology is a free resource for you, where you can find standards, guidelines, and best practices to manage cybersecurity-related risk. Its Cybersecurity Framework is a flexible, prioritized, and cost-effective approach that can help promote the protection and resilience of any company.
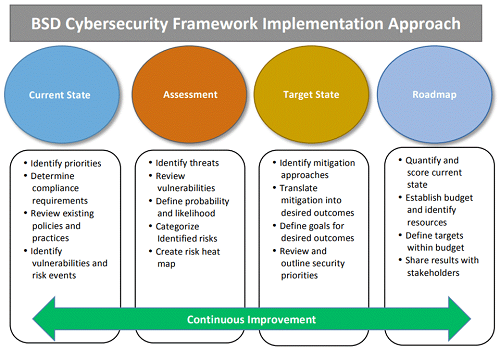
The framework also includes an implementation approach: a methodology for anyone to analyze possible opportunities to address areas that can be improved.
 |
|
Image from the National Institute of Standards and Technology |
Protecting your clients’ information requires a level of effort beyond the fiduciary responsibility of providing appropriate advice. Rolling up your sleeves and finding out both what you can do and what is already being done is the sign of a engaged financial adviser.
Al Wilson, Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM), is president emeritus of the nonprofit Philadelphia Alliance of InfraGard. InfraGard is a partnership between the FBI and members of the private sector, whose members include business executives, entrepreneurs, military and government officials, computer professionals, academics, and state and local law enforcement.
Accounting & Auditing
Cybersecurity Begins Inside Your Company
 By Al Wilson, CISSP, CISM
By Al Wilson, CISSP, CISM
The Verizon Breach Report offers several important lessons, one of which is that education regarding cyberattacks and the application of basic computer hygiene principles could have prevented about 88 percent of the more than 1,900 breaches that were analyzed within the report. Information security professionals understand this, and stress a balanced program of three guiding principles: availability, integrity, and confidentiality.
A major piece of any cyber defense is understanding that success is dependent on the interest and participation of the end users. Relying on someone else (IT departments, consultants, etc.) and assuming that computer security will be taken care of for you can lead to a tragic outcome. Reading several PICPA blog posts, it’s clear that many members have received excellent insight regarding what they can do to boost their own, and therefore the client’s security. (See “Modern Data Security Threats,” “Cloud Computing: Security and Risk Management,” and “Securing Data in the Cloud.”)
Of the three principles mentioned above, I will start with availability. In the end, the ability of a business to provide value to its clients is rooted in the ability to conduct business without interruption. While this is a topic that includes high availability (the ability to failover from system to system without interruption) and the ability to defend against denial-of-service attacks, at the most basic level is the concept of backup and recovery. Too often individuals believe that backups are being taken care of for them, or they assume someone in-house knows how to retrieve data. You must periodically test whether you can retrieve any or all of your data to a separate location. Doing so is the mark of a mature process.
Maintaining accuracy and completeness of information over its entire life is the basis of data integrity. In the area of advising on personal finances, you must make sure the data you receive is not altered in transit or in its storage location. Subsequent use of the information’s dissemination must also shield against alterations. It would behoove those in the industry to know and understand if this is being done and how it is being done on your behalf. Recent news reports indicate that some of the evidence against Paul Manafort, former Trump campaign manager, was obtained because he was unable to convert financial documents to PDFs. By sending documents back and forth via email, Manafort and his associates made it easy for prosecutors to determine that the documents had been altered, who they were altered by, and when.
The confidentiality of your information-protection program is arguably the one most visible and understandable area of defense among those in your company who aren’t dedicated to the information security field. Ask yourself the following questions:
- When I use email, should I just use a username and password, or should I adopt multifactor authentication?
The multifactor concept provides an extra layer of security if you get tricked into revealing your password via phishing or it gets guessed because it follows a simple pattern. The extra step could be a text back to your phone with a unique code, an app that provides a unique time-based code, or an app that merely asks you to “OK” a login. For example, the hack of the Democratic National Committee began as a phishing attack, which likely could have been mitigated if the two-step authentication of Google was turned on. - Do you or your team feel comfortable recognizing unusual requests?
Phishing and other social engineering tactics prey on people’s desire to help and their inattention to details. A common mode of operation includes compromising one of your vendors, then sending in requests for action under their guise. Make sure everyone in your corporate structure knows it is OK to pick up the phone and verify who the person is that the request is coming from and what their relationship is to what you do. - Do you know whether your computer systems are being patched for vulnerabilities? Is there a requested date/time for you to leave your computer on to receive patches, is there a scheduled downtime for the servers and websites that you depend on?
A common observation from IT personnel is that they don’t feel empowered by the company to do the necessary maintenance due to a corporate misperception that the system would be unavailable. Reports indicate that the Equifax breach was partially exasperated by not patching systems in a timely fashion. Perhaps understanding how things are done and giving support to those who might need it will save a lot of grief in the end.
 |
|
Image from the National Institute of Standards and Technology |
Want to learn more so that you can be a good partner to your clients and can ask the proper questions to your IT support staff? Or are you an independent adviser who would like to feel more confident regarding the program of protection you have? The National Institute of Standards and Technology is a free resource for you, where you can find standards, guidelines, and best practices to manage cybersecurity-related risk. Its Cybersecurity Framework is a flexible, prioritized, and cost-effective approach that can help promote the protection and resilience of any company.
The framework also includes an implementation approach: a methodology for anyone to analyze possible opportunities to address areas that can be improved.
 |
|
Image from the National Institute of Standards and Technology |
Protecting your clients’ information requires a level of effort beyond the fiduciary responsibility of providing appropriate advice. Rolling up your sleeves and finding out both what you can do and what is already being done is the sign of a engaged financial adviser.
Al Wilson, Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM), is president emeritus of the nonprofit Philadelphia Alliance of InfraGard. InfraGard is a partnership between the FBI and members of the private sector, whose members include business executives, entrepreneurs, military and government officials, computer professionals, academics, and state and local law enforcement.
Ethics
Cybersecurity Begins Inside Your Company
 By Al Wilson, CISSP, CISM
By Al Wilson, CISSP, CISM
The Verizon Breach Report offers several important lessons, one of which is that education regarding cyberattacks and the application of basic computer hygiene principles could have prevented about 88 percent of the more than 1,900 breaches that were analyzed within the report. Information security professionals understand this, and stress a balanced program of three guiding principles: availability, integrity, and confidentiality.
A major piece of any cyber defense is understanding that success is dependent on the interest and participation of the end users. Relying on someone else (IT departments, consultants, etc.) and assuming that computer security will be taken care of for you can lead to a tragic outcome. Reading several PICPA blog posts, it’s clear that many members have received excellent insight regarding what they can do to boost their own, and therefore the client’s security. (See “Modern Data Security Threats,” “Cloud Computing: Security and Risk Management,” and “Securing Data in the Cloud.”)
Of the three principles mentioned above, I will start with availability. In the end, the ability of a business to provide value to its clients is rooted in the ability to conduct business without interruption. While this is a topic that includes high availability (the ability to failover from system to system without interruption) and the ability to defend against denial-of-service attacks, at the most basic level is the concept of backup and recovery. Too often individuals believe that backups are being taken care of for them, or they assume someone in-house knows how to retrieve data. You must periodically test whether you can retrieve any or all of your data to a separate location. Doing so is the mark of a mature process.
Maintaining accuracy and completeness of information over its entire life is the basis of data integrity. In the area of advising on personal finances, you must make sure the data you receive is not altered in transit or in its storage location. Subsequent use of the information’s dissemination must also shield against alterations. It would behoove those in the industry to know and understand if this is being done and how it is being done on your behalf. Recent news reports indicate that some of the evidence against Paul Manafort, former Trump campaign manager, was obtained because he was unable to convert financial documents to PDFs. By sending documents back and forth via email, Manafort and his associates made it easy for prosecutors to determine that the documents had been altered, who they were altered by, and when.
The confidentiality of your information-protection program is arguably the one most visible and understandable area of defense among those in your company who aren’t dedicated to the information security field. Ask yourself the following questions:
- When I use email, should I just use a username and password, or should I adopt multifactor authentication?
The multifactor concept provides an extra layer of security if you get tricked into revealing your password via phishing or it gets guessed because it follows a simple pattern. The extra step could be a text back to your phone with a unique code, an app that provides a unique time-based code, or an app that merely asks you to “OK” a login. For example, the hack of the Democratic National Committee began as a phishing attack, which likely could have been mitigated if the two-step authentication of Google was turned on. - Do you or your team feel comfortable recognizing unusual requests?
Phishing and other social engineering tactics prey on people’s desire to help and their inattention to details. A common mode of operation includes compromising one of your vendors, then sending in requests for action under their guise. Make sure everyone in your corporate structure knows it is OK to pick up the phone and verify who the person is that the request is coming from and what their relationship is to what you do. - Do you know whether your computer systems are being patched for vulnerabilities? Is there a requested date/time for you to leave your computer on to receive patches, is there a scheduled downtime for the servers and websites that you depend on?
A common observation from IT personnel is that they don’t feel empowered by the company to do the necessary maintenance due to a corporate misperception that the system would be unavailable. Reports indicate that the Equifax breach was partially exasperated by not patching systems in a timely fashion. Perhaps understanding how things are done and giving support to those who might need it will save a lot of grief in the end.
 |
|
Image from the National Institute of Standards and Technology |
Want to learn more so that you can be a good partner to your clients and can ask the proper questions to your IT support staff? Or are you an independent adviser who would like to feel more confident regarding the program of protection you have? The National Institute of Standards and Technology is a free resource for you, where you can find standards, guidelines, and best practices to manage cybersecurity-related risk. Its Cybersecurity Framework is a flexible, prioritized, and cost-effective approach that can help promote the protection and resilience of any company.
The framework also includes an implementation approach: a methodology for anyone to analyze possible opportunities to address areas that can be improved.
 |
|
Image from the National Institute of Standards and Technology |
Protecting your clients’ information requires a level of effort beyond the fiduciary responsibility of providing appropriate advice. Rolling up your sleeves and finding out both what you can do and what is already being done is the sign of a engaged financial adviser.
Al Wilson, Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM), is president emeritus of the nonprofit Philadelphia Alliance of InfraGard. InfraGard is a partnership between the FBI and members of the private sector, whose members include business executives, entrepreneurs, military and government officials, computer professionals, academics, and state and local law enforcement.
Leadership
Cybersecurity Begins Inside Your Company
 By Al Wilson, CISSP, CISM
By Al Wilson, CISSP, CISM
The Verizon Breach Report offers several important lessons, one of which is that education regarding cyberattacks and the application of basic computer hygiene principles could have prevented about 88 percent of the more than 1,900 breaches that were analyzed within the report. Information security professionals understand this, and stress a balanced program of three guiding principles: availability, integrity, and confidentiality.
A major piece of any cyber defense is understanding that success is dependent on the interest and participation of the end users. Relying on someone else (IT departments, consultants, etc.) and assuming that computer security will be taken care of for you can lead to a tragic outcome. Reading several PICPA blog posts, it’s clear that many members have received excellent insight regarding what they can do to boost their own, and therefore the client’s security. (See “Modern Data Security Threats,” “Cloud Computing: Security and Risk Management,” and “Securing Data in the Cloud.”)
Of the three principles mentioned above, I will start with availability. In the end, the ability of a business to provide value to its clients is rooted in the ability to conduct business without interruption. While this is a topic that includes high availability (the ability to failover from system to system without interruption) and the ability to defend against denial-of-service attacks, at the most basic level is the concept of backup and recovery. Too often individuals believe that backups are being taken care of for them, or they assume someone in-house knows how to retrieve data. You must periodically test whether you can retrieve any or all of your data to a separate location. Doing so is the mark of a mature process.
Maintaining accuracy and completeness of information over its entire life is the basis of data integrity. In the area of advising on personal finances, you must make sure the data you receive is not altered in transit or in its storage location. Subsequent use of the information’s dissemination must also shield against alterations. It would behoove those in the industry to know and understand if this is being done and how it is being done on your behalf. Recent news reports indicate that some of the evidence against Paul Manafort, former Trump campaign manager, was obtained because he was unable to convert financial documents to PDFs. By sending documents back and forth via email, Manafort and his associates made it easy for prosecutors to determine that the documents had been altered, who they were altered by, and when.
The confidentiality of your information-protection program is arguably the one most visible and understandable area of defense among those in your company who aren’t dedicated to the information security field. Ask yourself the following questions:
- When I use email, should I just use a username and password, or should I adopt multifactor authentication?
The multifactor concept provides an extra layer of security if you get tricked into revealing your password via phishing or it gets guessed because it follows a simple pattern. The extra step could be a text back to your phone with a unique code, an app that provides a unique time-based code, or an app that merely asks you to “OK” a login. For example, the hack of the Democratic National Committee began as a phishing attack, which likely could have been mitigated if the two-step authentication of Google was turned on. - Do you or your team feel comfortable recognizing unusual requests?
Phishing and other social engineering tactics prey on people’s desire to help and their inattention to details. A common mode of operation includes compromising one of your vendors, then sending in requests for action under their guise. Make sure everyone in your corporate structure knows it is OK to pick up the phone and verify who the person is that the request is coming from and what their relationship is to what you do. - Do you know whether your computer systems are being patched for vulnerabilities? Is there a requested date/time for you to leave your computer on to receive patches, is there a scheduled downtime for the servers and websites that you depend on?
A common observation from IT personnel is that they don’t feel empowered by the company to do the necessary maintenance due to a corporate misperception that the system would be unavailable. Reports indicate that the Equifax breach was partially exasperated by not patching systems in a timely fashion. Perhaps understanding how things are done and giving support to those who might need it will save a lot of grief in the end.
 |
|
Image from the National Institute of Standards and Technology |
Want to learn more so that you can be a good partner to your clients and can ask the proper questions to your IT support staff? Or are you an independent adviser who would like to feel more confident regarding the program of protection you have? The National Institute of Standards and Technology is a free resource for you, where you can find standards, guidelines, and best practices to manage cybersecurity-related risk. Its Cybersecurity Framework is a flexible, prioritized, and cost-effective approach that can help promote the protection and resilience of any company.
The framework also includes an implementation approach: a methodology for anyone to analyze possible opportunities to address areas that can be improved.
 |
|
Image from the National Institute of Standards and Technology |
Protecting your clients’ information requires a level of effort beyond the fiduciary responsibility of providing appropriate advice. Rolling up your sleeves and finding out both what you can do and what is already being done is the sign of a engaged financial adviser.
Al Wilson, Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM), is president emeritus of the nonprofit Philadelphia Alliance of InfraGard. InfraGard is a partnership between the FBI and members of the private sector, whose members include business executives, entrepreneurs, military and government officials, computer professionals, academics, and state and local law enforcement.
Practice Management
Cybersecurity Begins Inside Your Company
 By Al Wilson, CISSP, CISM
By Al Wilson, CISSP, CISM
The Verizon Breach Report offers several important lessons, one of which is that education regarding cyberattacks and the application of basic computer hygiene principles could have prevented about 88 percent of the more than 1,900 breaches that were analyzed within the report. Information security professionals understand this, and stress a balanced program of three guiding principles: availability, integrity, and confidentiality.
A major piece of any cyber defense is understanding that success is dependent on the interest and participation of the end users. Relying on someone else (IT departments, consultants, etc.) and assuming that computer security will be taken care of for you can lead to a tragic outcome. Reading several PICPA blog posts, it’s clear that many members have received excellent insight regarding what they can do to boost their own, and therefore the client’s security. (See “Modern Data Security Threats,” “Cloud Computing: Security and Risk Management,” and “Securing Data in the Cloud.”)
Of the three principles mentioned above, I will start with availability. In the end, the ability of a business to provide value to its clients is rooted in the ability to conduct business without interruption. While this is a topic that includes high availability (the ability to failover from system to system without interruption) and the ability to defend against denial-of-service attacks, at the most basic level is the concept of backup and recovery. Too often individuals believe that backups are being taken care of for them, or they assume someone in-house knows how to retrieve data. You must periodically test whether you can retrieve any or all of your data to a separate location. Doing so is the mark of a mature process.
Maintaining accuracy and completeness of information over its entire life is the basis of data integrity. In the area of advising on personal finances, you must make sure the data you receive is not altered in transit or in its storage location. Subsequent use of the information’s dissemination must also shield against alterations. It would behoove those in the industry to know and understand if this is being done and how it is being done on your behalf. Recent news reports indicate that some of the evidence against Paul Manafort, former Trump campaign manager, was obtained because he was unable to convert financial documents to PDFs. By sending documents back and forth via email, Manafort and his associates made it easy for prosecutors to determine that the documents had been altered, who they were altered by, and when.
The confidentiality of your information-protection program is arguably the one most visible and understandable area of defense among those in your company who aren’t dedicated to the information security field. Ask yourself the following questions:
- When I use email, should I just use a username and password, or should I adopt multifactor authentication?
The multifactor concept provides an extra layer of security if you get tricked into revealing your password via phishing or it gets guessed because it follows a simple pattern. The extra step could be a text back to your phone with a unique code, an app that provides a unique time-based code, or an app that merely asks you to “OK” a login. For example, the hack of the Democratic National Committee began as a phishing attack, which likely could have been mitigated if the two-step authentication of Google was turned on. - Do you or your team feel comfortable recognizing unusual requests?
Phishing and other social engineering tactics prey on people’s desire to help and their inattention to details. A common mode of operation includes compromising one of your vendors, then sending in requests for action under their guise. Make sure everyone in your corporate structure knows it is OK to pick up the phone and verify who the person is that the request is coming from and what their relationship is to what you do. - Do you know whether your computer systems are being patched for vulnerabilities? Is there a requested date/time for you to leave your computer on to receive patches, is there a scheduled downtime for the servers and websites that you depend on?
A common observation from IT personnel is that they don’t feel empowered by the company to do the necessary maintenance due to a corporate misperception that the system would be unavailable. Reports indicate that the Equifax breach was partially exasperated by not patching systems in a timely fashion. Perhaps understanding how things are done and giving support to those who might need it will save a lot of grief in the end.
 |
|
Image from the National Institute of Standards and Technology |
Want to learn more so that you can be a good partner to your clients and can ask the proper questions to your IT support staff? Or are you an independent adviser who would like to feel more confident regarding the program of protection you have? The National Institute of Standards and Technology is a free resource for you, where you can find standards, guidelines, and best practices to manage cybersecurity-related risk. Its Cybersecurity Framework is a flexible, prioritized, and cost-effective approach that can help promote the protection and resilience of any company.
The framework also includes an implementation approach: a methodology for anyone to analyze possible opportunities to address areas that can be improved.
 |
|
Image from the National Institute of Standards and Technology |
Protecting your clients’ information requires a level of effort beyond the fiduciary responsibility of providing appropriate advice. Rolling up your sleeves and finding out both what you can do and what is already being done is the sign of a engaged financial adviser.
Al Wilson, Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM), is president emeritus of the nonprofit Philadelphia Alliance of InfraGard. InfraGard is a partnership between the FBI and members of the private sector, whose members include business executives, entrepreneurs, military and government officials, computer professionals, academics, and state and local law enforcement.
Technology
Cybersecurity Begins Inside Your Company
 By Al Wilson, CISSP, CISM
By Al Wilson, CISSP, CISM
The Verizon Breach Report offers several important lessons, one of which is that education regarding cyberattacks and the application of basic computer hygiene principles could have prevented about 88 percent of the more than 1,900 breaches that were analyzed within the report. Information security professionals understand this, and stress a balanced program of three guiding principles: availability, integrity, and confidentiality.
A major piece of any cyber defense is understanding that success is dependent on the interest and participation of the end users. Relying on someone else (IT departments, consultants, etc.) and assuming that computer security will be taken care of for you can lead to a tragic outcome. Reading several PICPA blog posts, it’s clear that many members have received excellent insight regarding what they can do to boost their own, and therefore the client’s security. (See “Modern Data Security Threats,” “Cloud Computing: Security and Risk Management,” and “Securing Data in the Cloud.”)
Of the three principles mentioned above, I will start with availability. In the end, the ability of a business to provide value to its clients is rooted in the ability to conduct business without interruption. While this is a topic that includes high availability (the ability to failover from system to system without interruption) and the ability to defend against denial-of-service attacks, at the most basic level is the concept of backup and recovery. Too often individuals believe that backups are being taken care of for them, or they assume someone in-house knows how to retrieve data. You must periodically test whether you can retrieve any or all of your data to a separate location. Doing so is the mark of a mature process.
Maintaining accuracy and completeness of information over its entire life is the basis of data integrity. In the area of advising on personal finances, you must make sure the data you receive is not altered in transit or in its storage location. Subsequent use of the information’s dissemination must also shield against alterations. It would behoove those in the industry to know and understand if this is being done and how it is being done on your behalf. Recent news reports indicate that some of the evidence against Paul Manafort, former Trump campaign manager, was obtained because he was unable to convert financial documents to PDFs. By sending documents back and forth via email, Manafort and his associates made it easy for prosecutors to determine that the documents had been altered, who they were altered by, and when.
The confidentiality of your information-protection program is arguably the one most visible and understandable area of defense among those in your company who aren’t dedicated to the information security field. Ask yourself the following questions:
- When I use email, should I just use a username and password, or should I adopt multifactor authentication?
The multifactor concept provides an extra layer of security if you get tricked into revealing your password via phishing or it gets guessed because it follows a simple pattern. The extra step could be a text back to your phone with a unique code, an app that provides a unique time-based code, or an app that merely asks you to “OK” a login. For example, the hack of the Democratic National Committee began as a phishing attack, which likely could have been mitigated if the two-step authentication of Google was turned on. - Do you or your team feel comfortable recognizing unusual requests?
Phishing and other social engineering tactics prey on people’s desire to help and their inattention to details. A common mode of operation includes compromising one of your vendors, then sending in requests for action under their guise. Make sure everyone in your corporate structure knows it is OK to pick up the phone and verify who the person is that the request is coming from and what their relationship is to what you do. - Do you know whether your computer systems are being patched for vulnerabilities? Is there a requested date/time for you to leave your computer on to receive patches, is there a scheduled downtime for the servers and websites that you depend on?
A common observation from IT personnel is that they don’t feel empowered by the company to do the necessary maintenance due to a corporate misperception that the system would be unavailable. Reports indicate that the Equifax breach was partially exasperated by not patching systems in a timely fashion. Perhaps understanding how things are done and giving support to those who might need it will save a lot of grief in the end.
 |
|
Image from the National Institute of Standards and Technology |
Want to learn more so that you can be a good partner to your clients and can ask the proper questions to your IT support staff? Or are you an independent adviser who would like to feel more confident regarding the program of protection you have? The National Institute of Standards and Technology is a free resource for you, where you can find standards, guidelines, and best practices to manage cybersecurity-related risk. Its Cybersecurity Framework is a flexible, prioritized, and cost-effective approach that can help promote the protection and resilience of any company.
The framework also includes an implementation approach: a methodology for anyone to analyze possible opportunities to address areas that can be improved.
 |
|
Image from the National Institute of Standards and Technology |
Protecting your clients’ information requires a level of effort beyond the fiduciary responsibility of providing appropriate advice. Rolling up your sleeves and finding out both what you can do and what is already being done is the sign of a engaged financial adviser.
Al Wilson, Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM), is president emeritus of the nonprofit Philadelphia Alliance of InfraGard. InfraGard is a partnership between the FBI and members of the private sector, whose members include business executives, entrepreneurs, military and government officials, computer professionals, academics, and state and local law enforcement.
Tax
Cybersecurity Begins Inside Your Company
 By Al Wilson, CISSP, CISM
By Al Wilson, CISSP, CISM
The Verizon Breach Report offers several important lessons, one of which is that education regarding cyberattacks and the application of basic computer hygiene principles could have prevented about 88 percent of the more than 1,900 breaches that were analyzed within the report. Information security professionals understand this, and stress a balanced program of three guiding principles: availability, integrity, and confidentiality.
A major piece of any cyber defense is understanding that success is dependent on the interest and participation of the end users. Relying on someone else (IT departments, consultants, etc.) and assuming that computer security will be taken care of for you can lead to a tragic outcome. Reading several PICPA blog posts, it’s clear that many members have received excellent insight regarding what they can do to boost their own, and therefore the client’s security. (See “Modern Data Security Threats,” “Cloud Computing: Security and Risk Management,” and “Securing Data in the Cloud.”)
Of the three principles mentioned above, I will start with availability. In the end, the ability of a business to provide value to its clients is rooted in the ability to conduct business without interruption. While this is a topic that includes high availability (the ability to failover from system to system without interruption) and the ability to defend against denial-of-service attacks, at the most basic level is the concept of backup and recovery. Too often individuals believe that backups are being taken care of for them, or they assume someone in-house knows how to retrieve data. You must periodically test whether you can retrieve any or all of your data to a separate location. Doing so is the mark of a mature process.
Maintaining accuracy and completeness of information over its entire life is the basis of data integrity. In the area of advising on personal finances, you must make sure the data you receive is not altered in transit or in its storage location. Subsequent use of the information’s dissemination must also shield against alterations. It would behoove those in the industry to know and understand if this is being done and how it is being done on your behalf. Recent news reports indicate that some of the evidence against Paul Manafort, former Trump campaign manager, was obtained because he was unable to convert financial documents to PDFs. By sending documents back and forth via email, Manafort and his associates made it easy for prosecutors to determine that the documents had been altered, who they were altered by, and when.
The confidentiality of your information-protection program is arguably the one most visible and understandable area of defense among those in your company who aren’t dedicated to the information security field. Ask yourself the following questions:
- When I use email, should I just use a username and password, or should I adopt multifactor authentication?
The multifactor concept provides an extra layer of security if you get tricked into revealing your password via phishing or it gets guessed because it follows a simple pattern. The extra step could be a text back to your phone with a unique code, an app that provides a unique time-based code, or an app that merely asks you to “OK” a login. For example, the hack of the Democratic National Committee began as a phishing attack, which likely could have been mitigated if the two-step authentication of Google was turned on. - Do you or your team feel comfortable recognizing unusual requests?
Phishing and other social engineering tactics prey on people’s desire to help and their inattention to details. A common mode of operation includes compromising one of your vendors, then sending in requests for action under their guise. Make sure everyone in your corporate structure knows it is OK to pick up the phone and verify who the person is that the request is coming from and what their relationship is to what you do. - Do you know whether your computer systems are being patched for vulnerabilities? Is there a requested date/time for you to leave your computer on to receive patches, is there a scheduled downtime for the servers and websites that you depend on?
A common observation from IT personnel is that they don’t feel empowered by the company to do the necessary maintenance due to a corporate misperception that the system would be unavailable. Reports indicate that the Equifax breach was partially exasperated by not patching systems in a timely fashion. Perhaps understanding how things are done and giving support to those who might need it will save a lot of grief in the end.
 |
|
Image from the National Institute of Standards and Technology |
Want to learn more so that you can be a good partner to your clients and can ask the proper questions to your IT support staff? Or are you an independent adviser who would like to feel more confident regarding the program of protection you have? The National Institute of Standards and Technology is a free resource for you, where you can find standards, guidelines, and best practices to manage cybersecurity-related risk. Its Cybersecurity Framework is a flexible, prioritized, and cost-effective approach that can help promote the protection and resilience of any company.
The framework also includes an implementation approach: a methodology for anyone to analyze possible opportunities to address areas that can be improved.
 |
|
Image from the National Institute of Standards and Technology |
Protecting your clients’ information requires a level of effort beyond the fiduciary responsibility of providing appropriate advice. Rolling up your sleeves and finding out both what you can do and what is already being done is the sign of a engaged financial adviser.
Al Wilson, Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM), is president emeritus of the nonprofit Philadelphia Alliance of InfraGard. InfraGard is a partnership between the FBI and members of the private sector, whose members include business executives, entrepreneurs, military and government officials, computer professionals, academics, and state and local law enforcement.








Leave a commentOrder by
Newest on top Oldest on top