Cybersecurity Opportunities for CPA Firms
It is mind-boggling to think what the future of technology holds, but the ever-present challenge is how to manage the relentless threats from cybersecurity intrusions. Cyberattacks are ranked as the top global risk to business leaders in advanced economies, and the takedown of a single cloud provider could cause $50 billion to $120 billion in economic damage.
by Paul R. Brazina, CPA, CGMA, CFF, Bruce A. Leauby, CPA, CMA, CFE, and Charles Sgrillo, CISSP, CEH Jun 1, 2022, 09:34 AM
 It is mind-boggling to think what the future of technology holds, but the ever-present challenge is how to manage the relentless threats from cybersecurity intrusions. Cyberattacks are ranked as the top global risk to business leaders in advanced economies, and the takedown of a single cloud provider could cause $50 billion to $120 billion in economic damage.1 As companies make progress in combating threats by securing their information, processes, and systems, hackers seem to be just as vigilant in finding new ways to exploit the new defenses. Businesses are challenged to create the appropriate strategy and adopt the most advanced tools to better foresee, recognize, and manage these risks.
It is mind-boggling to think what the future of technology holds, but the ever-present challenge is how to manage the relentless threats from cybersecurity intrusions. Cyberattacks are ranked as the top global risk to business leaders in advanced economies, and the takedown of a single cloud provider could cause $50 billion to $120 billion in economic damage.1 As companies make progress in combating threats by securing their information, processes, and systems, hackers seem to be just as vigilant in finding new ways to exploit the new defenses. Businesses are challenged to create the appropriate strategy and adopt the most advanced tools to better foresee, recognize, and manage these risks.
CPAs are in a unique position to help address these cybersecurity threats. Not only do their own firms face potential incursions, but there is an enormous opportunity to serve clients who share similar cybersecurity risks and related compliance obligations. PwC suggests that many firms are currently reacting and being defensive in addressing fraud prevention rather than being proactive. The firm notes, “only 54 percent of global organizations have conducted a general fraud or economic crime risk assessment in the past two years, and less than half had conducted a cybercrime risk assessment.”2 Only 30 percent of firms had any type of cybercrime response plan, so significant needs remain. Here is where an opportunity exists for CPA firms.
PCAOB and AICPA Respond
At its June 2018 meeting, the Standing Advisory Group of the Public Company Accounting Oversight Board (PCAOB) discussed cybersecurity issues and the implications for financial reporting and auditing, and stressed how auditors have a responsibility to ensure the integrity of financial reporting and evaluate the impact of cybersecurity breaches. The risk of a breach must be evaluated by a multidisciplinary team, including risk management specialists, the audit engagement team, a national assurance expert, the internal control team for financial reporting, the information assurance team, advisory services, and general counsel. No individual can possess all the necessary knowledge and skills, thus the team approach.3
The Audit Risk Model requires auditors to assess inherent risk, control risk, and detection risk to minimize the overall risk of an incorrect audit report. Cybersecurity intersects with inherent risk since product, customer, and vendor data may be compromised, causing significant financial loss to the company. Recent examples are numerous, and include companies such as MyHeritage (92 million records), TK/TJ Maxx (94 million records), Equifax (143 million records), and Adobe Inc. (152 million records).
Cybersecurity has a major impact on the risk that a breach of a company’s financial reporting system, if not detected, could cause material misstatements in a company’s records. Lack of adequate cybersecurity controls becomes a major issue for independent auditors.
The AICPA and the PCAOB are addressing the need for auditors to understand cybersecurity risks, incorporate cybersecurity risk assessment into their audit plans, and develop expertise for cyber-security examinations under the System and Organization Controls (SOC) suite of service offerings. Currently, these offerings (SOCs 1, 2, and 3) focus on internal controls in service organizations; whereas, a new SOC framework was developed for CPAs to report on cybersecurity.4
Considered in its simplest form, cybersecurity is an additional risk businesses must manage. Since CPAs are already specialists in risk assessment, it is a natural extension to broaden their expertise to include cybersecurity and take advantage of AICPA’s new cybersecurity risk management reporting framework. CPAs can help organizations communicate relevant and useful information about the effectiveness of their cybersecurity risk management programs to stakeholders.
In its framework, the AICPA acknowledges a fundamental tenet of cybersecurity: an entity that operates in cyberspace is likely to experience one or more security events or breaches at some point in time, regardless of the effectiveness of the entity’s cybersecurity controls.
Enterprise Risk Management Framework 
Before engaging in reporting activities, it is imperative that companies have an effective system of internal control to manage all risks that might impact their objectives, competitive advantage, and stakeholder value. Likely, COSO’s Internal Control – Integrated Framework (2013) or the Enterprise Risk Management (ERM) Integrated Framework (2004) provide the structure to evaluate and manage risks. The key is “manage” since the risk cannot be entirely avoided.6
The CPA and his or her clients may want to view their cyber profile through the five major components of the COSO framework (each major component contains two to five subcomponents).
Control environment – The overall corporate philosophy (tone at the top) determines whether the board and top management buy into managing risks and are willing to support programs that help mitigate this risk. This also helps ensure funding is available and policies support the appropriate risk program. This emphasizes cyber risk controls as a business problem, not an IT problem, and should be embraced by the entire organization.
Risk assessment – A key component is determining the firm’s risk appetite. This is the area that identifies, assesses, and prioritizes risk, and implements mitigation strategies and responses. This allows for alternative strategies or adjustment to objectives if the trade-offs to risk or security are too great.
Control activities – This is where most risk professionals spend their time developing control activities, policies, and procedures. As companies rely more on cloud-based storage and external data management vendors, integration with those outside vendors has become more common. It presents another potential threat by allowing an opening to company data. To counter this, firms should negotiate with vendors and third parties for the right to audit their cybersecurity practices as needed, or use a third party to audit. AICPA’s new reporting framework may be an opportunity, like auditing third-party service providers (payroll or trust services), but with a cybersecurity focus.
A key strategy in reducing cyber risk is training employees. The weakest link in any corporate system is employees, and hackers know it. Firms need to determine how best to make employees aware of the dangers lurking in their networks.
Cybercriminals often send blanket emails to large groups of users, hoping someone will take the bait and download an infected attachment or click on a bogus website. How can firms ensure employees are not lured into these traps? Developing clear policies and procedures is a first step, but creating the proper culture requires the active engagement of employees in preventive measures on an ongoing basis. There should be phishing tests, in which suspect emails are sent to employees to see who will respond or open a link. Then, appropriate feedback should be sent to employees reminding them that suspicious emails should be reported to the appropriate person in the company.
Multifactor authentication adds another layer of security by incorporating a username and password with a second level of information to access data (such as a text code sent to a cell phone). Thus, if someone is fooled into going to a fake website and entering a password, it will be useless to the criminals without the secondary information.
The practice of allowing employees to work remotely also creates a vulnerability outside of the corporate wall. Control over network access and user accounts is a high priority. Many companies are limiting employee access only to those areas needed to perform their job responsibilities.
Social media is everywhere. Since the use of social media does increase the risk of intrusions, companies have to decide whether or not to ban it, or, if allowed, to establish appropriate policies to develop, train, and control the engagement of employees for approved business practices.
Some studies show that over half of cybersecurity incidents come from insiders. Companies may need to consider policies that ask for consent to monitor at work, provide guidelines on downloading files or programs, and define rules on using personal devices on company systems.
Best practices related to cybersecurity need to be built into the regular daily activities of employees to sustain an effective cybersecurity culture.
Information: communications and reporting – The goal is to gather data (of which there is so much) and summarize it into meaningful and actionable information so a company can reach its objectives. Advanced analytics and data visualization tools are becoming more sophisticated at assisting in recognizing risks earlier. Things to consider here are which metrics should be used to measure the effectiveness of a cybersecurity control system and to compare and measure performance. Also, develop a system to raise awareness among personnel of cyber risks.
Monitor activities – Review and revise is standard practice in any control system. Procedures should be implemented to have continuous revise and improve procedures. This is an excellent area for CPA firms to be part of the solution process.
COSO’s ERM framework is well known in accounting firms, and it can help serve as a lens to view how the control system is designed and operating. ERM, however, is not a replacement for existing information security frameworks, and there are other resources available to the IT professional. The National Institute of Standards and Technology (NIST) of the U.S. Department of Commerce released many resources to set standards, guidelines, and best practices to reduce the potential threat of cyber risks. Related publications include NIST Special Publication 800-30, Guide for Conducting Risk Assessments, and Publication 800-39, Managing Information Security Risk.7 The Defense Federal Acquisition Regulation Supplement also made the NIST 800-171 controls series mandatory for governmental subcontractors to bolster the U.S. supply chain. This is just one example of how cybersecurity will become a component of every business’s risk management framework.
Consulting Opportunities for CPAs 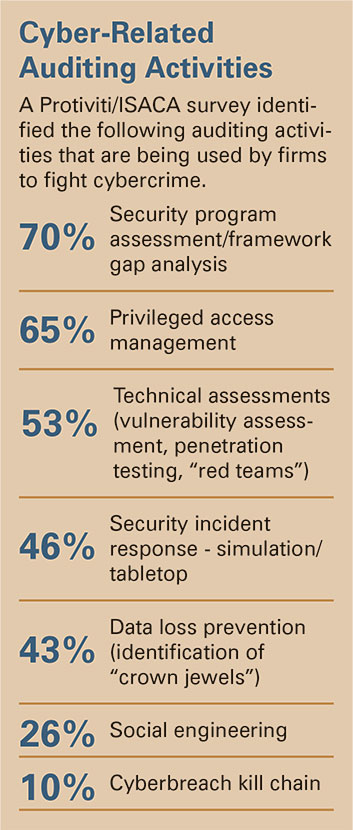
A major effort is being made by the AICPA to bridge the gap between the technical nature of cybersecurity and the ERM CPAs have used in the past. Over the past two years, the AICPA has taken steps to educate CPAs on the key risks surrounding cybersecurity, and how to observe businesses’ cyber processes and communicate discovered risks to those businesses. The AICPA introduced a cybersecurity certificate for CPAs to become effective communicators of cybersecurity risk, while gaining a general understanding of AICPA’s new cybersecurity risk management reporting framework.8
CPAs are often the first people a business will ask for guidance regarding risk management. The idea of a CPA playing a critical role in cybersecurity will exponentially increase as blockchain technology becomes integrated into financial processes. CPAs should also be educating clients on their fiduciary and legal responsibility to protect employee and client information. They should also be consulting clients on their cyber posture and ensuring adequate controls are in place. Businesses of every size can implement a simple, four-phase approach to cybersecurity:
- Assess – Every business must first understand its current risk profile before addressing any remediation plans. Has the business assessed its cyber risks in a formal risk assessment, using an industry-leading framework such as the NIST Cybersecurity Framework?
- Enhance – After the business assesses its risks, has it taken adequate and reasonable steps to remediate any risk discovered during the initial gap assessment? This can take the form of official cyber and information policies and procedures, employee awareness training, and systems upgrades.
- Manage – With every risk comes the task of continually managing the risk over time. This is no different in the case of cybersecurity. As the business continues to reevaluate its current cyber controls, is it defining clear metrics and goals that will show the growth of its cybersecurity risk management program? A perfect example of this is phishing awareness. Does the business sufficiently train its employees on phishing attacks? Can it show an initial baseline of its employees’ phishing awareness vs. the latest awareness assessment?
- Validate – An interesting part of cybersecurity is the process known as a penetration test. Once a business has evaluated its threats, implemented safeguards, and trained employees, it is now time to validate effectiveness. A penetration test attempts to evaluate the security of IT infrastructures using a controlled environment to attack, identify, and exploit vulnerabilities. These vulnerabilities may exist in operating systems, services, networks, or applications. They may also exist due to improper configurations or risky end-user behavior. Another form of validation is known as a cyber war game or tabletop exercise. In this scenario, advisers would conduct a tabletop exercise with both executive leadership and the IT mechanism to walk through a potential cyber risk event. The exercise helps evaluate whether a control exists to mitigate the risk. This differs from the penetration test, as these assessments are actively looking to test and confirm a control is in place.
Conclusion
CPAs have a major cybersecurity challenge: their assurance responsibility to understand their clients’ cybersecurity threats related to the financial internal control structure. However, having this knowledge opens an opportunity to provide value-added consulting services regarding cybersecurity assessment, enhancement, management, and validation skills.
1 A Global Look at IT Audit Best Practices: Assessing the International Leaders in an Annual ISACA/Protiviti Survey (2018).
2 Global Economic Crime and Fraud Survey, PwC (2018).
3 https://pcaobus.org/News/Events/Documents/Cybersecurity%20Briefing%20Paper.pdf
4 A CPA’s Introduction to Cybersecurity, AICPA.
5 SOC for Cybersecurity, AICPA.
6 www.coso.org/Pages/default.aspx
7 National Institute of Standards and Technology.
8 Course details can be found at www.picpa.org/certificates.
Paul R. Brazina, CPA, CGMA, CFF, is an assistant professor at La Salle University in Philadelphia. He is a member of the PICPA Education and Educator’s Conference committees. He can be reached at brazina@lasalle.edu.
Bruce A. Leauby, CPA, CMA, CFE, is an associate professor at La Salle University. He is a member of PICPA’s Forensic and Litigation Services and Business Valuation committees. He can be reached at leauby@lasalle.edu.
Charles Sgrillo, CISSP, CEH, is a certified ethical hacker and the cybersecurity manager and practice lead at Kreischer Miller in Horsham. He can be reached at csgrillo@kmco.com.

